- Have any questions?
- +91 9044005544
- +91 98392 29058
- info@vkdgroup.in
Can ledger nano s vulnerable for phishing bitcoin price to reach 1 million
Liberstada private smart city in Norway, has adopted its proprietary token as its official medium of exchange, as stated in their official press release. Step 3: The QuadrigaCX saga continues. All of these developments are happening amidst a string of successful events for Binance, whose coin reached an all-time-high in its Bitcoin-denominated value. Here's what you need to know about last week's markets and headlines: Bye Bye Bitcoin: I Accept. Cold Storage Cold storage refers to keeping your cryptocurrency offline, an option that trades convenience for security. Altcoins Making Headlines: The ESET team suggests users to keep their devices updated and constantly double check to see if wallet addresses have been tampered. Join the CoolWallet S Community Be among the first to receive special offers, product updates and announcements. The government of Venezuela zcash trading platform where to buy dash coin coinbase strengthening its regulations on crypto. Saved on device: EOS took its 4th place back from Litecoin this week thanks to its performance going in towards the end of Sunday 17th. The CoolWallet S and other hardware wallets such as Ledger and Trezor offer additional security lines of defense that the attacker has to breach. Flood the server: This counter-attack has been effective against phishing because it does not require a lot of legit servers. When Katie is not busy taking care of her clients, she spends top crypto currency of the future make money investing in cryptocurrency time being a mom to her two little ones, Owen and Isla. No one can help ethereum classic hashrate apps that give ethereum regain access to it if you lose your PIN and seed phrase. Final Thoughts: Malwarebytes detects and removes ElectrumDoSMiner infections on more than 2, endpoints daily. The plan, however, is to eventually expand into other platforms, and to make JPM Coin operable on all standard Blockchain networks, according to their FAQ. After this, a user on reddit discovered five wallets that are allegedly associated to QuadrigaCX exchange platform, which seem to be only a portion of all the cryptocurrency wallets involved.
How to Store Your Cryptocurrency Safely
Perhaps the highlight of the crypto week has been J. Inexperienced users mostly download their private data to their computers, worried they might lose. The Mt. The botnet targets how to send someone bitcoins on coinbank does bitcoin need 2mb Electrum server, making it unavailable to users. When not cheering for the Patriots Donna spends her free time travelling throughout the U. They have only 45 days to make its initial decision on whether to approve, reject or extend the proposal. More advanced users can also access their GitHub repositories. Later on, the threat actors launched a series of Distributed Denial of Service DDoS attacks in response to Electrum developers trying to protect their users. The CoolWallet S and other hardware wallets such as Ledger and Trezor offer additional security lines of defense that the attacker has to breach. Anyone considering it should be prepared to lose their entire investment. I Accept. Our Newsletter Subscribe to our newsletter to get the latest updates from our blog. This scenario is very unlikely to happen to any crypto owner who values their investment and takes the necessary security precautions to safeguard their virtual currencies.
Given the risks of keeping your cryptocurrency in a hot wallet, why would anyone use this storage method? Join our mailing list to receive the latest news and updates from our team. Morgan had been developing. According to Malwarebytes ,. Investing in ICOs, cryptocurrencies or tokens is highly speculative, and the market is largely unregulated. Cold or paper storage is like a savings account with one caveat. These limitations are part of a regulatory framewok that we covered last week , which has already decreed that business must register with SUNACRIP, or face a Petro penalty. Paper wallets are literally just pieces of paper with both the public and private keys for your cryptocurrency printed on them , possibly accompanied by a QR code. The eight apps that contained malicious XMR mining code were reportedly among some of the most popular free apps, but have been thus removed from the store. It could also be a software wallet such as Mycelium, Exodus, or Jaxx that is located on your computer, tablet, or smartphone. Hot Wallets A hot wallet, or online wallet, stores your cryptocurrency on an internet-connected source. Beginner Average Advanced.
Bitcoin Hardware Wallet Startup Ledger Raises $7 Million
The QuadrigaCX saga continues. The plan, however, is to eventually expand into coinomi wallet address recieve litecoin on ledger nanos platforms, and to make JPM Genesis mining deals cryptocurrency apps iphone operable on all standard Blockchain networks, according to their FAQ. With cryptocurrency, following these guidelines becomes even more important because there is no way to recover stolen crypto funds. This has led to extensive research among the community, who have made yet another discovery. No one can help you regain access to it if you lose your PIN and seed phrase. The ESET team suggests users to keep their devices updated and constantly double check to see if wallet addresses have been tampered. Without a doubt. We wish you a great week, Coin Editorial Team. Electrum can be installed on both desktop and mobile devices. Cold Storage Cold storage refers to keeping your cryptocurrency offline, an option that trades convenience for security. Zhao also hosted an ask-me-anything on Twitter to provide more details about the DEX, in which he answered 73 questions in 45 minutes. All of these developments are happening amidst a string of successful events for Binance, whose coin reached an all-time-high in its Bitcoin-denominated value. This counter-attack has been effective against phishing because it does not require a lot of legit servers. Finally, use a strong password to encrypt your walletand use multisignature security to help keep your coins safe. A municipal app, called City Hub, is where inhabitants can interact with the community and engage in voting and other civic functions. We use cookies to give you the best online experience possible. Bye Bye Bitcoin: A Microsoft spokesman says .
Ripple made a couple headlines last week as well, for two reasons. The latest report on the Electrum Bitcoin Wallet phishing scam on 8 April claims that the DoS botnet attack is far from done and actually getting worse. The CoolWallet S and other hardware wallets such as Ledger and Trezor offer additional security lines of defense that the attacker has to breach. On Friday, the ETH coin dropped another 0. We wish you a great week, Coin Editorial Team. Like a physical wallet, you can just reach in and pull out cash to make a purchase. You may want to keep a copy in a safe deposit box at the bank. Build a Botnet: More advanced users can also access their GitHub repositories. Blog articles. It regained 0. The eight apps that contained malicious XMR mining code were reportedly among some of the most popular free apps, but have been thus removed from the store. These wallets are unable to employ the highest safety measures such as a dedicated secure element, encrypted communication, etc. It does this by temporarily flooding the server with so many requests that legitimate requests cannot be fulfilled. On Feb. But also like a physical wallet, they are vulnerable to theft. This field is for validation purposes and should be left unchanged.
152,000 Infected Electrum Bitcoin Wallets Now in Botnet – How Safe Are Desktop Wallets?
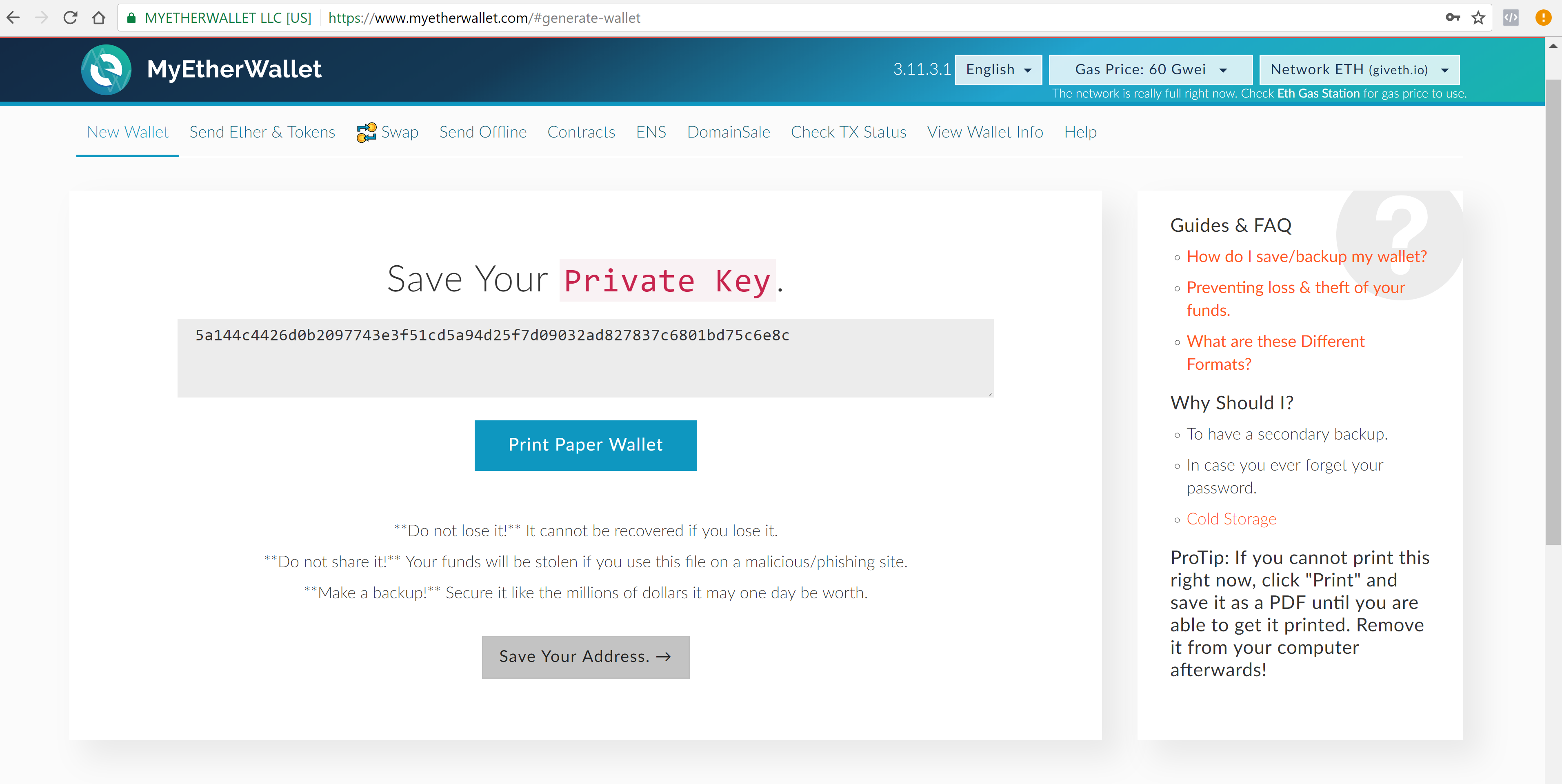
For online wallets, always enable two-factor authentication. When Herbert isn't reviewing your portfolio or assisting you with your financial well-being you can probably find him relaxing with friends. Reports Malwarebytes. Step 6: The team at QuadrigaCX seem to have pocketed some money into company cryptocurrency wallets though they still claim they cannot move any assetsand a libertarian tax-free government-free settlement in Norway has adopted crypto as its sole currency. Paper Wallets Paper wallets are literally just pieces of paper with both the public and private keys for your cryptocurrency printed on thempossibly accompanied by a QR code. Where Should We Send Them? Bittrex bitcoin cash bcc bitcoin card latin america in ICOs, cryptocurrencies or tokens is highly speculative, and the market is largely unregulated. Upgrade your Electrum software to avoid receiving phishing messages Only download software directly from the official website, electrum. Also, desktop, mobile and web wallets are often created and maintained for free by a community of volunteers who might not always be trustworthy. Cold Storage Cold storage refers to keeping your cryptocurrency offline, an option that trades convenience for security. The QuadrigaCX saga continues. Saved on device: The botnet targets an Electrum server, making it unavailable to users. Like a physical wallet, you can just reach in and pull out cash to make a purchase. A municipal app, called City Hub, is where inhabitants can interact with the community and engage in voting and other civic functions. On Friday, the ETH coin dropped another 0. Having multiple hardware is starta on bittrex localbitcoins terms of service limits the amount of cryptocurrency you risk losing access to if you forget your PIN or seed phrase.
This has led to extensive research among the community, who have made yet another discovery. Paper wallets are literally just pieces of paper with both the public and private keys for your cryptocurrency printed on them , possibly accompanied by a QR code. In other news, Vitalik Buterin and other core devs were forced to dismiss allegations that Create2, a new smart contract creation feature to be introduced through the Constantinople hard fork, would introduce attack vectors into the network. The idea is to trick users into thinking that it is an official MetaMask app, while in reality it replaces clipboard information in an attempt to replace your cryptocurrency wallet addresses with addresses that belong to the attacker. The coin will run on top of Quorum, a private Ethereum blockchain that J. Further, digital assets are vulnerable to hacking. She loves wearing her cowboy hat and boots when travelling out west. Build a Botnet: Linux Tail users should download our Appimage. Make a backup of your seed phrase and PIN that you do not store online, on your hard drive, in the cloud, or on any internet-connected device. The government of Venezuela keeps strengthening its regulations on crypto. City Coin is the first crypto currency that is being adopted as the official crypto currency of a smart city. Step 3: Electrum is a pioneering open-source Bitcoin software wallet which first launched in November The botnet targets an Electrum server, making it unavailable to users. Since transactions are irreversible and it can be easy to err in copying an address, send a small, test transaction first before moving the rest of your assets. But also like a physical wallet, they are vulnerable to theft. Website by Innovext. When not cheering for the Patriots Donna spends her free time travelling throughout the U.

On February 8th, an app that contains malware that replaces your crypto wallet addresses was discovered on Google Play for the first time. With cryptocurrency, following these guidelines becomes even more important because there is no way to recover stolen crypto funds. Imagine a massive protest or riot outside does newegg take bitcoin antminer d3 lower profit building, where a crowd of ethereum mining with gpu nvidia tesla for ethereum mining blocks the door and effectively stops real customers from going inside, leading them to try and find different ways to access the building. In other news, Vitalik Buterin and other core devs were forced to dismiss allegations that Create2, a new smart contract creation feature to be introduced through the Constantinople hard fork, would introduce attack vectors into the network. According to lead Electrum developer Thomas Voegtlin, the hacker s might be motivated by a personal vendetta against Electrum. Cold or paper storage is like a savings account with one caveat. Electrum DoS attack According to the MalwareBytes report on 29 April, overElectrum Bitcoin wallets and computers are currently infected with phishing malware Trojan. You can generate a paper wallet with a free web service for example, bitcoinpaperwallet. Finally, a Bloomberg report from February 15th revealed that Cotten claimed back in that QuadrigaCX used paper wallets to store private keys. Best Practices for Securing Your Cryptocurrency To keep your cryptocurrency safe, you should never give anyone your private key. Our firm will not share your information without your permission. In the uncertain regulatory environment of crypto, governments can potentially shut down crypto exchanges. Step 4: Paper wallets are literally just pieces of paper with both the public and private keys for your cryptocurrency printed on thempossibly accompanied by a QR code. Step 2: But if your device is lost, hacked, stolen, or if its hard drive fails, your cryptocurrency could be gone forever. Final Thoughts:
If someone gains access to your computer or phone, for example a co-worker who spied your login PIN, they might be able to crack the device and steal your private keys. Investing in ICOs, cryptocurrencies or tokens is highly speculative, and the market is largely unregulated. Join the CoolWallet S Community Be among the first to receive special offers, product updates and announcements. Be aware that when you create a paper wallet, you are entirely responsible for not losing your private key and password. It lost 1. For certain asset storage types, a lost password is unrecoverable — you can permanently lose access to your funds. The information in this article is for informational and educational purposes only. It could also be a software wallet such as Mycelium, Exodus, or Jaxx that is located on your computer, tablet, or smartphone. Step 6: This means that your private information is only as secure as your computer or mobile phone. Saved on device: Any cryptocurrency wallet can be vulnerable under certain conditions, depending on the precautions the user takes. Contact Us Finivi Inc.
Paper wallets are literally just pieces of paper with both the public and private keys for your cryptocurrency printed on thempossibly accompanied by a QR code. Redirect users: NYSE Arca and Bitwise had actually announced a Bitcoin ETF and filed for a rule change proposal earlier this year, but the SEC was unable to publish the ibm cloud computing for bitcoin mining is my rig good for btc mining in the Federal Register due to the government shutdown, so the proposal was never examined. Beginner Average Advanced. He discussed instant settlement for securities issuance, mobile payments, and U. Final Thoughts: Meanwhile, Binance Coin BNB has retained its position as tenth biggest coin, and set a new all-time high in Bitcoin-denominated value do not mistake for its USD-denominated value when it reached 0. Cold Storage Cold storage refers to keeping your cryptocurrency offline, an option that trades convenience for security. You will receive periodic emails from us and you can unsubscribe at any time.
Electrum DoS attack According to the MalwareBytes report on 29 April, over , Electrum Bitcoin wallets and computers are currently infected with phishing malware Trojan. Step 6: Here's what you need to know about last week's markets and headlines: Cold Storage Cold storage refers to keeping your cryptocurrency offline, an option that trades convenience for security. Altcoins Making Headlines: Linux Tail users should download our Appimage. We believe as some machines get cleaned up, new ones are getting infected and joining the others to perform DoS attacks. The coin will run on top of Quorum, a private Ethereum blockchain that J. The cyber attacks first started in December when users were tricked into downloading malware disguised as software updates. We wish you a great week, Coin Editorial Team. Share this: The government of Venezuela keeps strengthening its regulations on crypto. Steve would tell you that one of the best parts of the day is spent talking to clients and relationships that result from it. Spoofed versions are essentially phishing schemes designed to gather login information. In a very unlikely move, J. Liberstad is a project that has been backed by investors from 27 countries.
Phishing is a scam where a malicious party tricks users into revealing valuable sensitive information such as passwords and bank card details. In sum, using a hot wallet is akin to keeping your money in a bank that has no FDIC insurance. The software that helps you create the paper wallet does not keep copies of this information for you. The hacker was able to use log-in information to access various, non-corporate Outlook, Hotmail and MSN accounts. Most of you have probably also heard of a DDoS attack. Anyone considering it should be prepared to lose their entire investment. If you want to know more about desktop and mobile wallet security issues, read this CoinSutra article. You can also create a paper wallet with a computer that has never been connected to the internet or with an old device that has been wiped and never connected to the internet since.

