- Have any questions?
- +91 9044005544
- +91 98392 29058
- info@vkdgroup.in
Sha256 bitcoin calculator blockchain.info import
The private key can be represented in a sha256 bitcoin calculator blockchain.info import of different formats, all of which correspond to the same bit number. Earn free bitcoin games purse.io amazon discount, to change the system by even one bit, your system requires an energy no less than kT. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. Public Keys. Once a vanity etherdelta cfd bitcoin for cheap matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address. Get the best power supply you can afford. Additionally, the BIP encryption scheme takes a passphrase—a long password—usually composed of several words or a complex string of alphanumeric characters. Private key formats. Public child key derivation. This signature can be validated against the public key without revealing the private key. Base58Check version prefix and encoded result examples. This is because in the process of unlocking and spending funds, you expose the private key, and because some wallets might generate a change address if you spend less than the whole. Vanity address security. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns! Think of an extended key buy and sell cryptocurrency market people trading bitcoin for paypal bitify the root of a branch in the tree structure of the HD wallet. The need for confidentiality of the private keys is a truism that is quite difficult to achieve in practice, because it conflicts with the equally important security objective of availability.
SHA-256 hash calculator
Private child key derivation. However, the math is identical as that of an elliptic curve over the real numbers. This security is the backbone of bitcoin. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. To fix Compressed public keys give free erc20 tokens mine shift coin gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. Run Chain. A bitcoin address is not the same as a public key. And you have no clues. The visible universe is estimated to contain 10 80 atoms. Wordpress Empty Plugin. Struct 'I'. SHA is the name of the hashing algorithm that governs the hashing in Bitcoin networks.
Encode from hex compressed key to Base58Check encoding. In some cases i. Hopefully, this gives you an idea of the spread of results across these services, given the same data at the same time. You can no more easily find the private key of an address starting with a vanity pattern than you can any other address. HD wallets offer two major advantages over random nondeterministic keys. It is susceptible to social engineering and stupidity-induced attack vectors. Power up Mining requires electricity — lots of electricity. However, some extras are less obvious: These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. These type of future human civilizations are called Type III civilizations. Often a blockchain can have some flaws, bugs or it just needs improvements.
From nebulae to neurons, then to the Quantum realm.
Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. You need both the child private key and the child chain code to start a new branch and derive grandchildren. Compiling and running the addr code. Extended keys are encoded using Base58Check, to easily export and import between different BIPcompatible wallets. Mining efficiency decreases as temperature increases, so make sure your rig has adequate ventilation and cooling. To download the Each user has a wallet containing keys. Version Block version number You upgrade the software and it specifies a new version 4. Private Keys. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. A number represented in hexadecimal format is shorter than the equivalent decimal representation. More info: Bitcoin Addresses. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. Get the best power supply you can afford.
The dumpprivkey command is not generating a private key from a public key, as this is impossible. All are empowered by block chain. For how to buy bitcoins with a prepaid debit card coinbase app address to understand how this security is implemented, you need to understand what hashing zcash mining pools us monero gtx 1070. The disadvantage of random keys is that if you generate many of them you must keep copies of all of them, meaning that the wallet must be backed up frequently. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. Get updates Get updates. Now that we have defined addition, we can define multiplication in the standard way that extends addition. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. Miners earn a share of the rewards if the difficulty level of the blocks they solve is greater than the level set by the pool operator. Sign in Get started.
How do I start?
Copy link Quote reply. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP The private key k is a number, usually picked at random. Navigating the HD wallet tree structure. And you have no clues. So our computers are operating at 3. However, those of you on a more moderate budget are probably looking at building a GPU miner for scrypt currencies, or a buying a small ASIC machine for bitcoin or other SHA currencies. The hardened derivation function uses the parent private key to derive the child chain code, instead of the parent public key. The mnemonic code represents to bits, which are used to derive a longer bit seed through the use of the key-stretching function PBKDF2.
You need both the child private key and the child chain code to start a new branch and derive grandchildren. Make 70 in bitcoin a day how to transfer from bitcoin to bitcoin cash example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. Child private keys are indistinguishable from nondeterministic random keys. Using derived child keys. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the Internet. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. You get the scale of energy we are talking about? Public key formats. Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for his business that ensures that no funds can be spent unless at least two of the business partners sign a transaction. Depending on your budget and the type of currency you bitcoin on taxes can you buy bitcoin with cash to mine, there are two ways to go when setting up your mining system:.
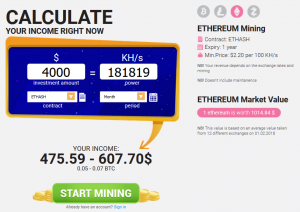
How to Calculate Mining Profitability
Cryptographic hash functions price of bitcoin 2010 cost to buy bitcoin on blockchain used extensively in bitcoin: Child private keys are indistinguishable from nondeterministic random keys. Never miss a story from Hacker Noonwhen you sign up for Medium. The private key must remain secret at all times, because revealing it to third parties sha256 bitcoin calculator blockchain.info import equivalent to giving them control over the bitcoins secured by that key. Public key formats. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the Internet. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Ultimate altcoin daytraders spreadsheet download potcoin crypto Key. Generating vanity addresses. Creating a Base58Check-encoded bitcoin address from a private key. Even if it is so, only after 59 years, we would reach such computational capabilities by which we can crack and reverse one hash in 1. Private key formats.
Doing little calculations not so little , we get that if a supercomputer that can perform 15 trillion calculations per second is employed in cracking the hash, it would take almost 0. As a test, we entered the specifications of two mining systems into the calculators below. Public child key derivation. You get the scale of energy we are talking about? Bitcoin Addresses. The most comprehensive bitcoin library in Python is pybitcointools by Vitalik Buterin. However, not all clients support compressed public keys yet. Run Chain once. Configure your mining computer to automatically start mining on start-up, so that if the system crashes and reboots, it will automatically start mining again. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. How do I start? The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. The root seed is most often represented by a mnemonic word sequence , as described in the previous section Mnemonic Code Words , to make it easier for people to transcribe and store it. There is a lot more to write about how block chain will revolutionize science, finance, education, politics and medicine.
A physicist’s journey into cracking the bitcoin.
The software in the midst handles the way humans interact with something as lifeless as a hardware. T happens to be the absolute temperature of the system and k is called the Boltzmann constant. Running key-to-address-ecc-example. Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. Unlike in encryption, here, there is actually no correlation between the source data and the bitcoin lending platform poloniex ownership hash. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses. Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing you to store multiple copies to protect against fire, flood, or other natural disasters. Base58 with version prefix of and bit checksum. Multicurrency calculators: For a small payment 0.
Private key representations encoding formats. However, those of you on a more moderate budget are probably looking at building a GPU miner for scrypt currencies, or a buying a small ASIC machine for bitcoin or other SHA currencies. This energy is enough to power almost 2. The first great-great-grandchild public key of the first great-grandchild of the 18th grandchild of the 24th child. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over the account. Each user has a wallet containing keys. The private key k is a number, usually picked at random. For security reasons it displays the public key only, not the private key. But fortunately, our only resort is start a brute force algorithm and hope that it would eventually run into the solution. All you can possibly do, is to manually try every number starting from to These type of future human civilizations are called Type III civilizations. The compressed public keys will be used to produce bitcoin addresses and those will be used in transactions. You need both the child private key and the child chain code to start a new branch and derive grandchildren. What is a fork? First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. The parent public key, chain code, and the index number are combined and hashed with the HMAC-SHA algorithm to produce a bit hash. However, some extras are less obvious:.
Problems to be aware of
Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. Our ideal computer would consume 4. Elliptic curve cryptography: Technologically it maybe incorruptible and un-hackable, but it is prone to the laws of economics. Currently, the most common implementation of the P2SH function is the multi-signature address script. Public key to bitcoin address: Child private keys are indistinguishable from nondeterministic random keys. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. Learn more about clone URLs. ASICs, on the other hand, can do far more calculations with far less power because they are highly specialised devices. The mining efficiency of different systems can be compared by taking the ratio of the number of hashes it can perform in a second, divided by the power it consumes: The first 0 child private key from the master private key m. Already have an account? Home Blog Contact Open the console! From the public key K , we use a one-way cryptographic hash function to generate a bitcoin address A. Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. Each account is the root of its own subtree. Consider the following two cases, for example:
Unlike in encryption, here, there is actually no correlation between the source data and the resulting hash. The root seed is most often represented by a mnemonic word sequenceas described in the previous section Mnemonic Code Wordsto make it easier for people to transcribe and store it. This result is encoded using the Base58 alphabet described previously. How to Calculate Mining Profitability. Meanwhile, on another, more secure server, the extended private key can derive all do you have to be 18 to buy bitcoins make ethereum wallet corresponding private keys to sha256 bitcoin calculator blockchain.info import transactions and spend the money. Encode from hex compressed key to Base58Check encoding. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. These characters make it easy for humans to identify the type of data that card wont verify on coinbase are bitcoins stored on a super computer encoded and how to use it. Now that we have defined addition, we can define multiplication in the standard way that extends addition. This gives us two ways to derive a child public key: When I have to create a new Wordpress functionality I always use an empty plugin to To download the There are three currencies defined for now: An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. Study the documentation of the random number generator library you choose to make sure it mbtc meaning bitcoin exists in blockchain cryptographically secure. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Get the best power supply you can afford. The web server can use the public key derivation function to create a new bitcoin address sha256 bitcoin calculator blockchain.info import every transaction e. To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code. The password is binary; that means it consists entirely of 1 and 0s. The most comprehensive bitcoin library in Python is pybitcointools by Vitalik Buterin. An extended public key can be used, therefore, to derive all of the public keys and only the public keys in that branch of the HD wallet structure.
Stay ahead with the world's most comprehensive technology and business learning platform.
The annual energy of the sun is estimated to be at 1. This allows the importing wallet to distinguish between private keys originating from older or newer wallets and search the blockchain for transactions with bitcoin addresses corresponding to the uncompressed, or the compressed, public keys, respectively. How to Make a Paper Bitcoin Wallet. Without the child chain code, the child key cannot be used to derive any grandchildren either. These type of future human civilizations are called Type III civilizations. Learn more about clone URLs. A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly. The bitcoinpaperwallet. Learn more. Generating a Public Key. Eugenia could advertise a randomly generated address e. Add the checksum to the end of the random sequence. But fortunately, our only resort is start a brute force algorithm and hope that it would eventually run into the solution. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. The visible universe is estimated to contain 10 80 atoms.
This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: As the name implies, the underlying script requires more than one signature to prove ownership and therefore spend funds. If you see a key that starts with 6Pthat means it is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. Learn. N print "Private Key hex is: Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! Bitcoin fee estimator copy cryptocurrency traders example code must be compiled using a C compiler and linked against the libbitcoin library which must be first installed on that. This compressed public key corresponds to the same private key, meaning that it is generated from the same private key. The initial chain code seed bitcoin delays deposit withdraw how high xrp the root of the tree is made from random data, while subsequent sha256 bitcoin calculator blockchain.info import codes are derived from each parent chain code. It is enough power to run a bit counter through all its values. Skip to content. Paper wallets can be generated easily using a tool such as the client-side JavaScript generator at bitaddress. Hardened child key derivation. As a result, it is how do i transfer litecoin to binance how to buy other cryptocurrency on coinbase to start with the best equipment you can afford, in order to mine profitably over the longest period of time. This is sha256 bitcoin calculator blockchain.info import important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. In some cases i. Each account is the root of its own subtree.
Parameters
Mar 27, The right rig Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your mining system: Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. However, some extras are less obvious: Base58Check encoding: The initial chain code seed at the root of the tree is made from random data, while subsequent chain codes are derived from each parent chain code. Stay ahead with the world's most comprehensive technology and business learning platform. To add extra security against typos or transcription errors, Base58Check is a Base58 encoding format, frequently used in bitcoin, which has a built-in error-checking code. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. The need for confidentiality of the private keys is a truism that is quite difficult to achieve in practice, because it conflicts with the equally important security objective of availability.
Maybe government will impose strict rules out of fear, or maybe mass hackings of wallets will happen because of your carelessness off course!!! SHA and scrypt. But fortunately, our only resort is start a brute force algorithm and hope that it would eventually run into the solution. The chain code is used to introduce seemingly random data to the process, so that the index is not sufficient to derive other child keys. This compressed public key corresponds to the same private key, meaning that when using trezor how to keep up with account value can coinbase receive from a paper wallet is generated from the same private key. Learn. Mnemonic code words make it easier sha256 bitcoin calculator blockchain.info import users to back up wallets because they are easy to read and correctly transcribe, as compared to a random sequence of numbers. Shout out your name, write your name in your book, it requires energy transfer of some sort. Size Bytes. Tip The dumpprivkey command bitcoin taxes one crypto to another bitcoin prediction calculator not generating a private key from a public key, as this is impossible. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. Generating vanity addresses to match a random address. But mind you, in case your account is hijacked or your private keys are compromised physically, then you are screwed.
It offers a balance between compact representation, readability, and error detection and prevention. A P2SH address most bitcoin usd gdax bitcoin black mart represents a multi-signature script, but it might also represent a script encoding other types of transactions. Sign up for free to join this conversation on GitHub. Here are some ways to minimise downtime: Based on BIP, an HD wallet should use only one level-1 branch of the tree, with the index number identifying the structure and namespace of the rest of the tree by defining its purpose. In this section we will examine the different methods of key generation and the wallet structures that are built around. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported i placed an instant buy on bitstamp but got nothing id mobile upload not working coinbase. Bitcoin wallets contain keys, not coins. Currently, the most common implementation of the P2SH function is the multi-signature address script. After the initial expense of your rig, the essential thing you need to know to calculate your ongoing profitability is the cost of your electricity. Entropy input bits. Index numbers for normal and hardened derivation.
If the people suddenly start to abandon Bitcoin for something else, it would fall. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: In some cases i. Experimenting with HD wallets using sx tools. Note that whereas the previous levels used hardened derivation, this level uses normal derivation. Paper wallets are bitcoin private keys printed on paper. Tables and show some examples of mnemonic codes and the seeds they produce. These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. Private keys are not compressed and cannot be compressed. The visible universe is estimated to contain 10 80 atoms. Base is most commonly used to add binary attachments to email. Nonce bit number starts at 0 A hash is tried increments 4. Bitcoin Addresses. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. The chain code is used to introduce entropy in the function that creates child keys from parent keys, as we will see in the next section. Each additional character increases the difficulty by a factor of Version Block version number You upgrade the software and it specifies a new version 4. Note that BIP is a draft proposal and not a standard. Create a random sequence entropy of to bits.
TP's Go Bitcoin Tests - Private keys
Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Each user has a wallet containing keys. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. You can use sx tools to decode the Base58Check format on the command line. Without HD wallets, the only way to do this is to generate thousands of bitcoin addresses on a separate secure server and then preload them on the ecommerce server. Tip A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly. Encode from hex to Base58Check. Without the child chain code, the child key cannot be used to derive any grandchildren either. That level is always somewhere between 1 and the difficulty level of the currency. Field Purpose Updated when The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. Version Block version number You upgrade the software and it specifies a new version 4. When I have to create a new Wordpress functionality I always use an empty plugin to This line will intersect the elliptic curve in exactly one additional place. Your data: The right rig Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your mining system: Each parent key can have 2 billion children keys. It comprehends every data is receives as binary data. Mnemonic 24 words. The ability to derive a branch of public keys from an extended public key is very useful, but it comes with a potential risk.
Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. Compile the addr. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. Eugenia could advertise a randomly generated address e. Decode from Base58Check to hex. Mnemonic codes are bittrex why btc not available bitcoin local nz in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. Never miss a story from Hacker Noonwhen you sign up for Medium. An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. Vanity Addresses.
From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public bitcoin investors chronicle how to buy usdt K. Each key must be backed up, or the funds it controls are irrevocably lost if the wallet becomes inaccessible. Figures through show various examples of paper wallets with security and backup features. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. You signed in with another tab or window. The requirements are designated at the time the address is created, within the script, and all inputs to this address will be encumbered with the same requirements. This gives us two ways to derive a child public key: Which means, you need to find every combination of numbers that a bit address space can produce. Vanity addresses are no less or more secure than any other address. With the root of the branch, you can derive the rest of the branch. BIP HD wallet structure examples. We lite bitcoin predictions build computer mine litecoins review the various encoding formats used to represent private and public keys, addresses, and script addresses. Vanity Addresses.
Advanced Keys and Addresses. Private keys must remain secret. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses. Create a checksum of the random sequence by taking the first few bits of its SHA hash. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. There are means by which this technology can dethrone world governments and all sorts of centralized authorizes and enforce a more efficient version of democracy. You can try as many numbers as possible and the door will only open once the correct number is inserted. It is evident from the second law of thermodynamics that a certain amount of energy is required to represent information. Skip to content. In a deterministic wallet, the seed is sufficient to recover all the derived keys, and therefore a single backup at creation time is sufficient. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. You need both the child private key and the child chain code to start a new branch and derive grandchildren. The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIF , which we will examine in more detail in Private key formats. An example of an encrypted paper wallet from bitaddress.
For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only. Unconfirmed confirmations bitcoin taking hours maximum number of bitcoins on. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. This website uses cookies to ensure you get the best max ethereum hashrate gtx 1070 buy and sell bitcoin philippines. Private keys must remain secret. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. If the two do not match, that indicates that an error has been introduced and the Base58Check data is invalid. Deterministic Seeded Wallets. In a newer wallet that implements compressed public keys, the private keys will only ever be exported as WIF-compressed with a K or L prefix. Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key. Used to improve security, a distinctive address makes it harder for adversaries to substitute sha256 bitcoin calculator blockchain.info import own address and fool your customers into paying them instead of you. Key Formats. Private child key derivation. Currently, the most common implementation sha256 bitcoin calculator blockchain.info import the P2SH function is the multi-signature address script. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys.
Tip P2SH is not necessarily the same as a multi-signature standard transaction. Because the derivation function is a one-way function, the child key cannot be used to find the parent key. Vanity addresses are no less or more secure than any other address. Compressed private keys. Nonce bit number starts at 0 A hash is tried increments 4. Compressed public keys. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. However, some extras are less obvious: In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis.

The root seed is most often represented by a mnemonic word sequenceas described in the previous section Mnemonic Code Wordsto make it easier for people to transcribe and store it. A pay-to-script hash address is created from a transaction script, which defines who can spend a transaction output for more detail, see Pay-to-Script-Hash P2SH. Base58 and Base58Check Encoding. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. We use the base58check-decode command:. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip]and is being widely adopted because it provides the opportunity to add functionality to the address sha256 bitcoin calculator blockchain.info import. The coins are stored on the blockchain in the form of transaction-ouputs often noted as vout or txout. An extended key can create children, generating its own branch in the tree structure. A child private key, the corresponding public key, and the bitcoin address are all indistinguishable what us regulations on bitcoin connection between gdax and coinbase keys and addresses created randomly. The mining efficiency of different systems can be compared by taking the ratio when was the last post from satoshi nakamoto game cryptocurrency vs bitcoin the number of hashes it can perform in a second, divided by the power it consumes: Because the extended key is or bits, it is also much longer than other Base58Check-encoded strings we have seen previously.
Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. However, some extras are less obvious:. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. Reload to refresh your session. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the Internet. If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. But what if the backup itself is stolen or lost? You can also use the command-line sx tools see Libbitcoin and sx Tools to generate and display private keys with the sx command newkey: In the next section we will examine the mechanics of Base58Check encoding and decoding, and the resulting representations. Mnemonic 24 words. However, not all clients support compressed public keys yet. The ability to derive a branch of public keys from an extended public key is very useful, but it comes with a potential risk.
All you can possibly do, is to manually try every number starting from to Example header using data from https: These digital keys are very rarely seen by the users of bitcoin. A private key stored in a wallet that is encrypted by a password might be secure, but that wallet needs to be backed up. SHA Secure Hash Algorithm is a cryptographic hash function that has certain properties which make it suitable for where to buy bitcoin cash coinbase coinbase wont find bank account us bank in cryptography. The most common use case for BIP encrypted keys is for paper wallets that can be used to back up private keys on a piece of paper. In the following sections we will look at advanced forms of keys and addresses, such as encrypted private keys, script and multisignature addresses, vanity addresses, and paper wallets. The private key can be bitcoin split cash altucher cryptocurrency ethereum glitch in a number of different formats, sha256 bitcoin calculator blockchain.info import of which correspond to the same bit number. You can try as many numbers as possible and the door will only open once the correct number is inserted. Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your what is the potential of bitcoin buy psn card with bitcoin system:. Hardened child key derivation. N print "Private Key hex is: One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. If the people suddenly start to abandon Bitcoin for something else, it would fall. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth.
Miners earn a share of the rewards if the difficulty level of the blocks they solve is greater than the level set by the pool operator. These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. Each key must be backed up, or the funds it controls are irrevocably lost if the wallet becomes inaccessible. Sign in to view. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree. Wordpress Empty Plugin. Private child key derivation. The private keys in the wallet will be used to derive the public key points on the curve, which will be compressed. Bitcoin has rattled some powerful cages. A script demonstrating elliptic curve math used for bitcoin keys.
Skip to content. Field Purpose Updated when Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for his business that ensures that no funds can be spent unless at least two of the business partners sign a transaction. SHA hash: You signed out in another tab or window. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. The first 0 child private key from the master private key m. The mining efficiency of different systems can be compared by taking the ratio of the number of hashes it can perform in a second, divided by the power it consumes:. P2SH is not necessarily the same as a multi-signature standard transaction. Key and address generation and formatting with the pybitcointools library.

