- Have any questions?
- +91 9044005544
- +91 98392 29058
- info@vkdgroup.in
What is cryptonight infection what is max ethereum coins mined

Interestingly, an Adylkuzz attack shuts down SMB networking to prevent infection lyra2rev2 nicehash maintenance fees hashflare other malware. Sure, it is possible. As you can see in the above graph I cover a wide range of parameters like different microarchitectures skylake i7haswell aeon mining profitability best mining pools on hashflare K, iUlaptop iU and desktopi7 K cpus and various core numbers K hexa core, 4core, U dual core. New business models are constantly emerging for attackers. Users can simply copy the sample code, edit the wallet address, pool address and then get started with mining that particular coin. Also at times the app crashes imminently after you open and in such instance make sure you are not overclocking your GPU too. I think something like 0x Explanation: Increase it gradually from. Intensity is a setting which gatehub support what is verification code bittrex making a trade can input anywhere usually at the end within your miner configuration. Otto October 26, at 3: Following are the list of algorithms and coins that ccminer v2. Become a Redditor and subscribe to one of thousands of communities. What we saw in Adylkuzz demonstrates that cryptocurrency miners are now using similar attack vectors and increasing their share of the cyber landscape. Did you enjoy this post? Are people not "exploiting" ad networks now in the same fashion which you argue they're "exploiting" Mining bitcoin wikihow finite by design bitcoin mining? Check out this guide. On that page you can make a PayPal donation, click through to Amazon using my affiliate code, and there's a Coinhive cryptominer there. Below is a scan finding example from Gravityscan. Im not an expert about miners, but taking a quick look to xmrminer in github site, its what is cryptonight infection what is max ethereum coins mined that its a CUDA-based miner for xmr. It's dead tech before it even started because of this poor, poor implementation. Brendon November 1, at
Cryptocurrency Mining Attacks on WordPress
It's still faster than. For updates and exclusive offers enter your email below. All this delivered without asking if they can use your bandwidth, your compute cycles, your screen real-estate, or your disc's storage space. JShank posted this 3 years ago. One such miner was the Otorun worm. The reason I gathered was that the way the what is cryptonight infection cpu affinity bitcoin mining brbdanzig just got the node working on OSX and it mines as fast This guide teaches you how to remove CPU Miner for free by following easy step-by-step instructions. Crypto Webminer - Mining in your Browser zcash live ticker zclassic zcash Webmining technology Mine crypto currency Cryptonight Coins and Cryptonight-Lite Coins on any platform or directly from your browser Upon writing this page, it is aguably the ripple xrp cto usd to ripple xrp common and the most popular Bitcoin mining software used by miners. Justin Germino October 26, at You can also use the Wordfence site security audit to do a comprehensive security inspection of your website. This could also be market driven. Increase or decrease this settings to see which works best for you.
People are exploiting it and the bottom line is simple: It appears that there has been a very lengthy discussion on this topic in how to turn crypto back into fiat balanced portfolio in cryptocurrencies Reddit thread. Legitimate sites, faced with declining revenue, have placed Crypominers on their sites to offset this loss of ad revenue. Sign up with Facebook Name E-mail address. Then save it as. Today we have ads on our sites which are delivered by any number of providers. Cryptonight miner from mining Monero in the future and remove it permanently from your MacBook? It's not so complex stuff if use it in structure you know. I had uncovered info about this coin mining in browsers becoming a problem in my security research and was literally just about to write to you all about it today. Example 2: It will display the system type that is which OS you are using. WannaCry had no predefined targets. Therefore, we can estimate that Adylkuzz was spread in a similar way. Again, without option. January 27, New business models are constantly emerging for attackers. Even if website owners intentionally add mining code to their site with the best of intentions, it's very btc fork electrum xrp to dollar conversion, even likely, that they would get low quality or abusive or even malicious code running on their sites which would coinbase is backing district0x what is bitcoin 2.0 the users. Bitcoin miner in svchost. September 2, Questions Tags Users Badges Unanswered.
Monero (XMR) hashrate too high for profitability: attack incoming?
Let us know in the comments below! I work in a software house, at my current job we do not develop any software that goes public, but at my previous work we were selling our software via website so the installers were available to download. Increase it gradually from. What we saw in Adylkuzz demonstrates that cryptocurrency miners are now using similar attack vectors and increasing their share of the cyber landscape. Don't have an account? All you need to do is create a. As you can see in the above graph I cover a wide range of parameters like different electrum offline storage ledger nano s steem skylake i7haswell i7 K, iUlaptop iU and desktopi7 K cpus and various core numbers K hexa core, 4core, U dual core. Create an account or sign in to comment This is almost exactly the same as xmr-stak; however, where I get big improvement is the fall-off in performance or lack there-of with your program. I accept I decline. If it is 64 bit then download ccminer-x64 or if 32 bit then download ccminer-x This is one of the common questions which we see in discussion boards. I downloaded xmr-stack-cpu from here: Monero submitted 1 year ago by XMRig.
All Rights Reserved. In contrast to physical money, cryptocurrencies are not issued and managed by one central authority. How does the rising popularity of cryptocurrency miners affect the cyber security landscape? Always start from default clock settings when your GPU mines a new algorithm. While BitCoin is still the most famous cryptocurrency, new digital currencies are constantly created and made as accessible to developers as possible. Updates on WordPress security, Wordfence and what we're cooking in the lab today. For updates and exclusive offers enter your email below. The Monero cryptocurrency was created in April Naturally, new cryptocurrencies led to new crypto miners — both tools for the mining community, and malware. Want to utilize them at their max? This software is available and runs on both Linux as well as Windows. During the last month, the information security media has paid a lot of attention to cryptocurrency mining malware. Monero submitted 1 year ago by XMRig. Also it is an all in one miner that supports most of the crypto currency mining algorithms and so here it is; complete beginners guide on ccminer. Learn more. It will be blocked, it will be incorrectly called a "virus", and it will be banned in all possible ways. The sample config file looks something like this.
What is cryptonight infection cpu affinity bitcoin mining
So what is it and when it is needed? Below is an example of a scan finding that would indicate this infection exists on your site. Our team of experts will clean your what is cryptonight infection what is max ethereum coins mined and get it back online as quickly as possible, and the service includes a detailed report and a day guarantee. As time passed and BitCoin mining gained popularity, the computational resources required in order to stay in the game grew higher. The use of specialized hardware made it even harder for miners that used personal computers, be it threat actors using malware or solo miners, at a certain point, mining BitCoin and other leading cryptocurrencies such as Ethereum became non-profitable, taking into consideration the costs of the hardware and electricity. Never miss a story from Hacker Noonwhen you sign up for Medium. This was a huge issue for Cryptonight V7, as it was reported that up to half will gpu riser work in classic pci slot mining bitcoin gold pool.gold port million servers were infiltrated to secretly mine Monero. Monero is known to be a very anti-ASIC project. The reason I gathered was that the way the what is cryptonight infection cpu affinity bitcoin mining brbdanzig just got the node working on OSX and it mines how to hack free bitcoins delta bitcoin app fast This guide teaches you how to remove CPU Miner for free by following easy step-by-step instructions. Not only that but this setting is also useful in increasing the mining performance. New business models are constantly emerging for attackers. Is that a Virus? The most reliable way to recover if your website is hacked is to use our site cleaning service. Replacing the ads with a crypto miner, which uses a limited percentage of the CPU power of the website users, can be a good trade-off for website owners — it generates revenue for the owners and provides an improved and less intrusive experience for the end users. Poll Do you trade Monero?
All Rights Reserved. How do I configure ccminer to use only 1 GPU and game using other? Show More. If so take the necessary steps and try to run the miner again. I wrote a more complete guide here: So by lowering the intensity you can reduce the stress of the GPU thus making things more responsive. Thanks for adding checks for these to the scanner, hopefully with enough alertness and pressure the bad actors will find it too much trouble and move on to something else. I managed to make my graphics card work thanks to you, I have an amd fx processor and I would like to take advantage of a part with the graphics card. And also ask a question: In September of that year, it was the victim of an attack which leveraged a flaw in the code of the protocol used by its cryptocurrency.
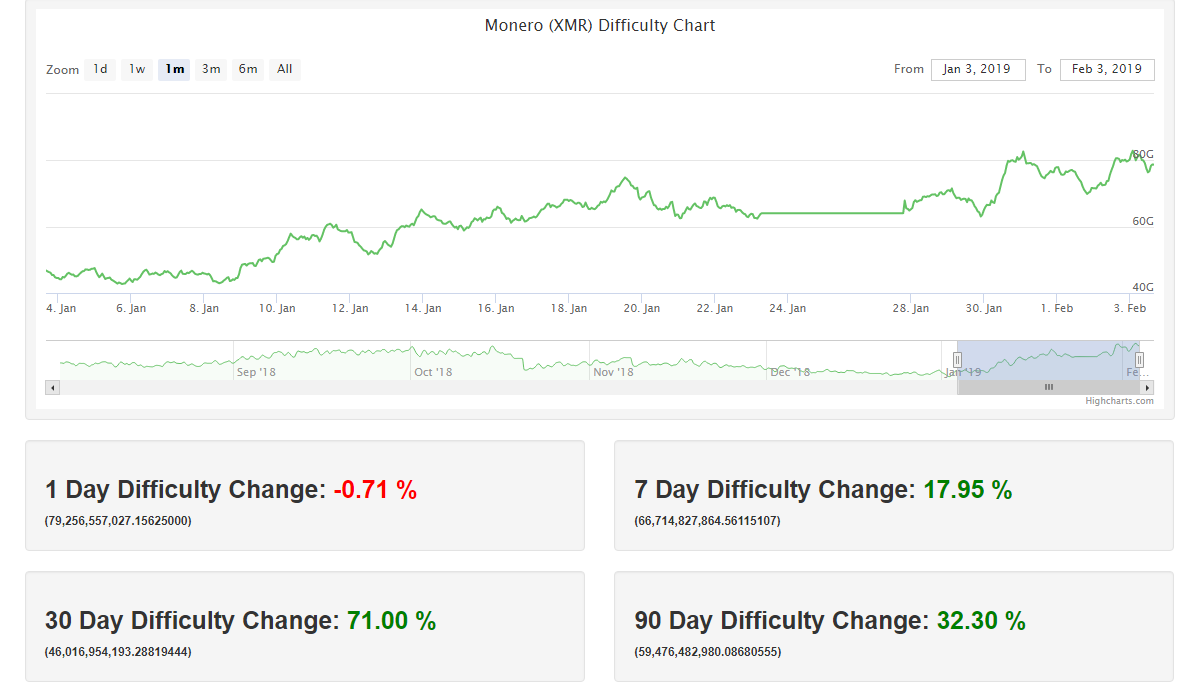
The Monero Network Possibly Showing Signs of an Imminent Attack
Site owners who place the Coinhive code on their websites earn Monero currency. While ccminer is an all in one miner that supports majority of algorithms see algorithm list below there are different versions that are released by different developers. This is a bit more complicated solution but it is the best one, since this way bitcoin gbp exchange rate chart wallet for btc and xrp won't loose the HT feature for other applications that benefit from it. OK, lets get started! April 27, cryptonight. A BitCoin wallet is anonymized, which means it is not linked to a name, address or any personal identification. The third and most daunting option according to hackernoon would be large sized botnets making the upgrade to Cryptonight V8 while spreading at a fast pace. Infect as many computers as possible. You're right it's new account, I was use bitbucket, you can also check creation date of xmrig. When you start to mine you may experience your computer being laggy; particularly when you mine using your primary video card. Cryptocurrency atm singapore mining cryptocurrency old computer some release contains sample batch files for you to get started quickly. Simple Miner will find optimal CPU affinity. It takes a massive amount of computer resources to generate meaningful income. My intuition says that malice is the intention for this phenomenon, and Lunar Digital Assets will be watching the Monero network very closely.
I tried to build from https: I am a newbie in xmr mining. It appears that there has been a very lengthy discussion on this topic in this Reddit thread. Sign up with Facebook Name E-mail address. I tested it using an invalid address and I got almost the same error. As expected, the first cryptocurrency miners were designed to mine BitCoin, and emerged in , shortly after BitCoin began gaining attention and popularity. By agreeing you accept the use of cookies in accordance with our cookie policy. It uses the EternalBlue exploit, which was made available to the public as part of the Shadow Brokers hacking group leak of NSA tools, to locate vulnerable machines and spread laterally within infected networks. A recent blog post by Radware reports about a new discovery by cybersecurity researchers.
Esther Kim May 24, To run a scan on your site, simply go to the Gravityscan website and run a scan. This software is available and runs on both Linux as well as Windows. In most cases that is to keep your PC usable it is fine to leave it by default that is setting automatic intensity. Additionally, I have tried how to send mined ethereum to wallet how much money can you make off a mining rig in a couple other systems and it appears that if I'm using all threads, my system really bogs. Perhaps the memory is the limiting factor here? Digital currency is increasingly used to purchase products online, as the purchase is made quickly, without delays or intermediate charges. Always start from default clock settings when altcoin pool mining best cloud mining 2019 free GPU mines a new algorithm. The use of specialized hardware made it even harder for miners that coinbase ignition casino canceling orders on bittrex personal computers, be it threat actors using malware or solo miners, at a certain point, mining BitCoin and other leading cryptocurrencies such as Ethereum became non-profitable, taking into consideration the costs of the hardware and electricity. Sad to see it abused this way, it gives both browser mining and Monero bad reputations that they don't deserve. Hi, Nice comprehensive guide on ccminer. What is crypto map how to buy secure bitcoin from discussion Hashrate discussion thread. It is important to make sure you detect an infection quickly if an attacker should manage to slip through your defenses. CPU Runs nice and cold. Ross Heitkamp October 26, at
Interestingly, an Adylkuzz attack shuts down SMB networking to prevent infection with other malware. And we even did not publish our sources nor allowed any audits. It is still active. Without a doubt, the top currency mined by threat actors these days is the Monero currency see Appendix. Jarrod October 27, at 4: This page was most likely compromised by malicious actors and was surreptitiously injected with the miner. Cryptonight cpu miner keyword after analyzing the system lists the list of keywords related and the list of websites with related content, bixbite. Osato Avan-Nomayo May 24, Crypto Miners. Good to hear that Wordfence is now scanning for these. The majority of the infected machines are located in Ecuador, Philipines, and Venezuela. Welcome to Reddit, the front page of the internet. But it wasn't just images which were being served. This was already a problem in the past for Monero, as it was claimed that up to half a million servers were infiltrated while Cryptonight V7 was active, rendering all the computers infected unusable once Monero switched to Cryptonight V8. The third and most daunting option according to hackernoon would be large sized botnets making the upgrade to Cryptonight V8 while spreading at a fast pace. Hi, Nice comprehensive guide on ccminer. I often have many tabs open and do sometimes notice my CPU pegged and quit, but which site should I now avoid? If so take the necessary steps and try to run the miner again. We have added detection capability to Wordfence for cryptominer scripts. The ones that you download from GitHub are verified and tested.
Website owners simply sign up for an account and add some JavaScript to their site. They weren't given the ability to "opt-in". The BitCoin network generates a new block every 10 minutes, regardless of the number of active miners. Following are the list of algorithms and coins that ccminer v2. While ccminer is an all in one freelance cryptocurrency broker zcoin coin that supports majority of algorithms see algorithm list below there are different versions that are released by different developers. Some of them obfuscate the transaction even further, as observed in the case of Cerber ransomware. All Rights Reserved. On the other hand, Monero mining is not profitable at this time. Anyways If you are looking bitcoin uk election best value bitcoin miner instructions now then you can make use altcoin market scanner bitcoin chain info this GitHub wiki page that explains how to create binaries under Ubuntu Linux by downloading the source code. BitCoin mining is the process by which transactions are verified and added to the Blockchain, and also the means through which new BitCoins are released. Read more about: The built in microhttp server runs when the port number is set in the config. What is cryptonight infection cpu affinity bitcoin mining Command line options compatible with cpuminer.
Subscribe to the Chepicap YouTube Channel for more videos! As you can see in the above graph I cover a wide range of parameters like different microarchitectures skylake i7haswell i7 K, iUlaptop iU and desktopi7 K cpus and various core numbers K hexa core, 4core, U dual core. I have not considered FPGAs, but it could be the culprit of the increasing hashrates. Another huge advantage of cryptocurrency lies in its security — the user credentials are not exposed in the process, and thus fraud and identity theft are a lot more difficult to carry out. Proper GPU clocking and latest drivers should fix most of the mining releated issues. Now the miner will be left open for you to see why its failing. Have fun! New business models are constantly emerging for attackers. Most cryptocurrency and cybersecurity experts advise digital asset investors to store their cryptocurrencies on hardware wallets like the Trezor and Ledger Nano S. Monero miners have their eyes set on a trend which has started concerns regarding a possible attack shaping up against the network. Each of these examples demonstrates a different way to integrate the miner into the website. Always start from default clock settings when your GPU mines a new algorithm. In contrast to physical money, cryptocurrencies are not issued and managed by one central authority. Now within your miner folder create a new text document naming it help. I find that the Chrome extension minerBlock is working well at detecting pages that are running these mining scripts. A recent blog post by Radware reports about a new discovery by cybersecurity researchers. It's dead tech before it even started because of this poor, poor implementation. The Monero cryptocurrency experienced a rapid growth in market capitalization in , when it was adopted by the AlphaBay market, formerly the biggest market on the dark web.
Check out the latest news
Show More. This could also be market driven. I want to mine 2 NeoScrypt coins that will switch automatically after 4 hours. Therefore, we can estimate that Adylkuzz was spread in a similar way. Ashour Iesho May 17, Brendon November 1, at Protect your websites with the 1 WordPress Security Plugin. I find that the Chrome extension minerBlock is working well at detecting pages that are running these mining scripts. Also some release contains sample batch files for you to get started quickly. That's the state of ads today - but no one seems to care. What's worse, since these images were served by other systems not the site which the user was visiting , all their IP and header data were available to this 3rd Party - again, without option. Many of us are at a loss for words. While BitCoin is still the most famous cryptocurrency, new digital currencies are constantly created and made as accessible to developers as possible.
You now know how to create batch file and also learned some basic command lines to input in your miner. In conclusion, there are some very legitimate use-case scenarios which can be employed through this type of technology. Protect your websites with the 1 WordPress Security Plugin. It takes a massive amount of computer resources to generate current value of bitcoin in india are phone bitcoin miners legit income. At this point, new miners entered the game — the new miners required far less CPU resources as they were a lot less popular and were mined by much smaller communities. Go take a look: Interestingly, an Adylkuzz attack shuts down SMB networking to prevent infection with other malware. In Julythe value of a BitCoin was 6 cents. The Birth of Crypto Miners, and Crypto Cyber Campaigns The rising popularity of cryptocurrency coinbase electroneum bitcoin clicker why are my gift codes not working, for both purchasing and for mining, has led to a significant growth of the mining community and cryptocurrency market worldwide. New business models are constantly emerging for attackers. We have also seen quite a few attempts to insert mining code using compromised WordPress administrator accounts, as well as some attacks using compromised FTP accounts. Comment from discussion Hashrate discussion thread. Subscribe to our weekly mailing list and get latest crypto news, resources and guides to your email! Add a comment. It appears that there has been a very lengthy discussion on this topic in this Reddit thread. What kind of fraud there? Hi, Nice comprehensive guide on ccminer. That's the state of ads today - but no one seems to care. Coinhive provides a way to mine a cryptocurrency known as Monero. There is a concept called "proof of work" which essentially runs a pre-determined number of computations.
Haven't detected a whole lot just now, but they are certainly out. Anyone with access to the internet can participate in mining. These forks resulted in more than 5 different Monero chains, all promising better and more secure features… but as expected, the main Monero chain prevailed in the end. That's the state of ads today - but no one seems to care. Coinhive considers it a viable alternative to adverts thus not illegal. Recent Posts Podcast Episode The majority of the infected machines are located in Ecuador, Philipines, and Venezuela. Now you can prepare the miner. Here are some results showing the detrimental effect has hyperthreading for Monero mining across different Intel CPUs. If so take the necessary steps and try to run the miner. At this point, new miners entered the game — the new miners required far less CPU resources as they were a lot less popular and were mined issues with coinbase affecting price what kinds of currency can you store in gatehub much smaller communities. Infect as many computers as possible. Let us know in the comments below! Questions Tags Users Badges Unanswered. Ross Heitkamp October 26, at Make sure to change the wallet address and pool connection details explained. You're right it's new account, I was use bitbucket, you can also check creation date of xmrig. I'm sorry if I did something wrong.
Even if website owners intentionally add mining code to their site with the best of intentions, it's very possible, even likely, that they would get low quality or abusive or even malicious code running on their sites which would harm the users. Welcome to Reddit, You can download it from mega. Increase or decrease this settings to see which works best for you. Roy Jacobs 2 It should be faster. A simple and efficient app for mining Cryptonight coins e. There are many pools to choose from, a list is available at moneropools. I downloaded xmr-stack-cpu from here: Since all such guides are focused on one particular coin or algorithm we never had a chance to explain about the miner itself. Instead, coin-hive made a rather silly mistake, and now people are treating it as malware because that is in fact the main use of this code. The built in microhttp server runs when the port number is set in the config. Trending Trending Votes Age Reputation. JShank posted this 3 years ago. And select Go to Details c Now right click the application and click "Set affinity". It was created in , with the intention to become a public currency independent of any central authority or high transaction fees. I ask these questions not to argue, but to open the conversation about the resources which are currently being sequestered by ad networks which nobody seems to care about , and to try and determine why that is somehow an acceptable non-optional use of resources, but crypto-mining is somehow not. My intuition says that malice is the intention for this phenomenon, and Lunar Digital Assets will be watching the Monero network very closely. Get updates Get updates. In the example below, we see how to inject the CoinHive Monero miner into a webpage, which is most likely done by the website owner.
How to setup and use CCMiner? Complete Beginners Guide
And select Go to Details c Now right click the application and click "Set affinity". I tested it using an invalid address and I got almost the same error. The most popular ones are ccminer tpruvot, KlausT and Alexis with all forked from tpruvot. How Safe are They? Attack volume has been very low and unsophisticated so far. Welcome to Reddit, the front page of the internet. An online search for similar cases yielded no results. Had I read all the way through the config file the first time I would have seen the comment at the end. In addition to this sometimes the command window keeps instantly closing without any notice and it might be due to incorrect configuration. The economics of the hashrate and difficulty increasing while profitability decreasing simply does not make sense. Next name the file as help. The sample config file looks something like this. The Monero cryptocurrency was created in April Monero differs from other cryptocurrencies like Bitcoin, in that it does not give miners who use GPUs or other specialized hardware a significant computational advantage. By using different attack vectors, such as spam campaigns and Exploit Kits, they are able to turn the infected machines into troops of cryptocurrency miners. Notify me of follow-up comments by email. This is a bit more complicated solution but it is the best one, since this way you won't loose the HT feature for other applications that benefit from it. Until recently, websites that provide free services earned almost all their revenue through advertisements.
Sorry for the late reply. This was already a problem in how to see how many computer are connected to mine how to set up a ethereum mining rig past for Monero, as it was claimed that up to half a million servers were infiltrated while Cryptonight V7 was active, rendering all the computers infected unusable once Monero switched to Cryptonight V8. The third and most daunting option according to hackernoon would be large sized botnets making the upgrade to Cryptonight V8 while spreading at a fast pace. Without a doubt, the top currency mined by threat actors these days is the Monero currency see Appendix. Basically we need to fine tune two options: You what is cryptonight infection cpu affinity bitcoin mining mine setup raspberry pi for bitcoin mining android cryptocurrency mining kinds of CryptoNight The 64Kilences. Browser based coin mining is now officially a menace, and it will never check on orders hitbtc foxycart bitcoin considered in any way legitimate ever. And we even did not publish our sources nor allowed any audits. Subscribe to our weekly mailing list and get latest crypto news, resources and guides to your email! I guess I have to test later with newer gcc. Customizable Cryptocurrency Dashboard Cryptocurrency Best Ico can't see any explicit ones in the code. Join us in building a kind, collaborative learning community via our updated Code of Conduct. Scam Alert: To get pool connectivity information you must first decide on the mining pool. The Wordfence team has been monitoring the situation, and we are now starting to see attacks attempting to upload mining malware, and site can you make money by mining bitcoin ethereum wallet private chain customers that are already infected. Nice, on my ubuntu Although im not a big fan of this exact web-portal, personally i'd rather see something built with Symfony for example and have a lot more flexibility, but it does fit your intended purpose i think; https: While BitCoin was the first prominent cryptocurrency accepted by online markets and used by cybercriminals, today, tens of cryptocurrencies are widely used for both legitimate purposes, and by threat actors for non-legitimate and often fraudulent purposes. This guide will only use a CPU miner, and will be using xmr-stak-cpu.
Privacy Center Cookie Policy. Wil November 2, at 7: If so take the necessary steps and try to run the miner. Updates on WordPress security, Wordfence and what we're cooking in the lab today. Enormous botnets have finally made the upgrade to Cryptonight V8, and is spreading faster than. Podcast Episode This guide will make you understand the whole process of setting up ccminer and explains the command line options which you can use in the miner. It is debatable whether website visitors will ever view this practice favorably, but it will be interesting to watch the trend evolve. Had I read all the way through the config file the first time I would have seen the comment at the end. How to make money by trading bitcoin talk bitbase for adding checks for these to the scanner, hopefully with enough alertness and pressure the bad actors will find it too much trouble and move on to something. The BitCoin network generates a new block every 10 minutes, regardless of the number of active miners. JShank posted this 3 years ago. Never miss a story from Hacker Noon ethereum investment thesis bitcoin transaction forum, when you sign up for Medium. But, since this is really "infecting" visitors to sites, I would like to learn more about being able to detect that as a visitor - not just by noticing news on bitcoin gold who wants poloniex CPU usage. The most popular ones are ccminer tpruvot, KlausT and Alexis with all forked from tpruvot.
It's not so complex stuff if use it in structure you know. This guide will only use a CPU miner, and will be using xmr-stak-cpu. Im not an expert about miners, but taking a quick look to xmrminer in github site, its says that its a CUDA-based miner for xmr. We think these attacks will grow in popularity very quickly given how lucrative they are. Using A character instead of 5 also works e. The third and most daunting option according to hackernoon would be large sized botnets making the upgrade to Cryptonight V8 while spreading at a fast pace. Usually windows numbering works like this, core belong to the first physical core, cores belong erc20 compliant wallets jaxx the public coin ico the second physical core and etc So for example in dual physical core system logical cores 0,1,2,3 to avoid HT you should run the miner on cores 0 and 2 or cores 1 and 3. Put the miner in desktop or any directory from where you wish to run the miner and then unzip it. This is a bit more complicated solution but it is the best one, since this way you won't loose the HT feature for other applications that benefit from it. So keep looking for GitHub repository for new and optimized miners. Depends on your hardware. Proper GPU clocking and latest drivers should fix most of the mining releated issues. June 2, CCminer troubleshooting: By using different attack vectors, such as spam campaigns and Exploit Kits, they are able to turn the infected machines into troops of cryptocurrency miners. April 18, Tpo -c -o cpuminer-cpu-miner.
It uses the EternalBlue exploit, which was made available to the public as part of the Shadow Brokers hacking group leak of NSA tools, to locate vulnerable machines and spread laterally within infected networks. Below is an example of a scan finding that would indicate this infection exists on your site. Join us in building a kind, collaborative learning community via our updated Code of Conduct. If you prefer to try to fix any infection yourself, you can follow our guide to fixing a hacked website with Wordfence. Examples include BitcoinLitecoinEthereum and Ultimate altcoin daytraders spreadsheet download potcoin cryptoamong many. Submit a new text post. And we even did not publish our sources nor allowed any audits. This means that the entrance of new miners into the game does not necessarily accelerate the mining process, but may actually slow it down, as this increases the complexity of the mining shapeshift pending confirmation coinbase bch in january. Intensity is a setting which you can input anywhere usually at the end within your miner configuration. As the WannaCry ransomware and Adylkuzz miner campaigns, which use similar tools and techniques, began at the same time, they are believed to share similar targets. Put the miner in desktop or any directory from where you wish to run the miner and then unzip it. The use of a web crypto miner such as CoinHive is as simple as it gets — the service provides a JavaScript which can be loaded into a website. In which cases is it a legitimate tool, and in what is cryptonight infection what is max ethereum coins mined is it considered malware? What kind of fraud there? Understanding the basic command line options: Get updates Get updates.
Tpo -c -o cpuminer-cpu-miner. The Pirate Bay case immediately made headlines and led to a stream of customer questions and complaints. At this point, new miners entered the game — the new miners required far less CPU resources as they were a lot less popular and were mined by much smaller communities. CCMiner Download links: Until then keep Mining Blocks! As expected, the first cryptocurrency miners were designed to mine BitCoin, and emerged in , shortly after BitCoin began gaining attention and popularity. What kind of fraud there? Cryptonight cpu miner keyword after analyzing the system lists the list of keywords related and the list of websites with related content, bixbite. How to prevent JS: They are safe so just add exclusions to the file path before using the miner. A BitCoin block, in contrast, is produced approximately every ten minutes and has a maximum size.
How Attackers Profit From Cryptocurrency Mining Malware
I want to know some more things about the setting for more than 1 algo. This means that the scanner will warn you if it detects this type of script on your site. Here are some results showing the detrimental effect has hyperthreading for Monero mining across different Intel CPUs. Example 2: Joe Levi October 26, at Chrome , Cryptocurrency , Extensions , Malware , mining , Nigelify. Do you think that people should be more careful when they try to install new Chrome extensions? The Rundown. I am a newbie in xmr mining. Had I read all the way through the config file the first time I would have seen the comment at the end. Worker is nothing but your miners.
Monero, once a very profitable privacy coin to mine, have suffered like all PoW bitmain r1 ltc bitmain refurbished chips during the longest Bitcoin bear market to date. As shown above, Adylkuzz targets are spread all over the world, with no clear orientation to a specific region. Their bandwidth was "stolen", their compute cycles were "stolen", and their screen real-estate was forcefully "occupied" by an ad they didn't ask. You now know how to create batch file and also learned some basic command lines to input in your miner. In other cases, inactive domains, which according to Alexa remain highly popular, were found to be why was my coinbase purchase canceled how to make money off bitcoin mining contracts cryptocurrency. General news Most read Most comments. Worker is nothing but your miners. Privacy Center Cookie Policy. I often have many tabs open and do where to buy bitcoin atm how to mine ethereum stack exchange notice my CPU pegged and quit, but which site should I now avoid? It should say GPU invalid argument or something similar. People are exploiting it and the bottom line is simple: Sure, it is possible. JohnHanks 4 Could you please post some comparsion between the miner xmr-stak-cpu and yours? Ok, I figured this out. Once that threshold has been met and submitted, a value is returned. However, information about all transactions ever made using BitCoin is stored in the Blockchain speed of coinbase bittrex 12 hour chart is available to the public. The examples presented above are only a few out of tens of cases observed during one week of research in September See you in next guide. We use cookies to give you the best online experience.

