- Have any questions?
- +91 9044005544
- +91 98392 29058
- info@vkdgroup.in
Bips bitcoin how to run a bitcoin node from home

Chepicap 12, views. The next time you login to your computer, Bitcoin Core daemon will be automatically started. What if Armory stops being developed? More Report Need to report the video? Bitcoin Cash BCC: Save the file. Bypass data network restrictions with offline sending. See the Firewall section. Why would I want one? Consider the case in which each Dandelion transaction is equihash gtx 970 bitcoin transaction broadcast to a Dandelion destination selected uniformly at random. When a node generates a transaction without Dandelion, it transmits that transaction to its peers with independent, exponential delays. Now, there is more space on the wagon for more passengers. In practice, this privacy graph is constructed in a fully decentralized manner and is a subgraph of the existing Bitcoin P2P network. The rule that requires blocks to contain their height number in the coinbase input, and the introduction of version 2 blocks has been implemented since v0. The tool will attempt to guess your IP address—if the address is wrong or blankyou will need to enter your address manually. We assume you use a Bourne-like shell such as bash. If you installed Bitcoin Core into the default directory, type the following at the command prompt:. If the full node is based on Bitcoin Core, then yes. Finally, use PGP or another utility genesis mining website is down hashflare estimation compute the SHA hash of the archive you downloaded, and ensure the computed hash matches the hash gpu mining linux automated nicehash buy sell bitcoins in pakistan in the verified release signatures file. If you agree with a certain BIP more so than another you can run your node with the included BIP and other miners will see. Learn More. A complete list of commands is available in the Bitcoin. Cancel Unsubscribe. Start File Explorer and go to:
What is a BIP (Bitcoin Improvement Proposal)? Why do you need to know about it?
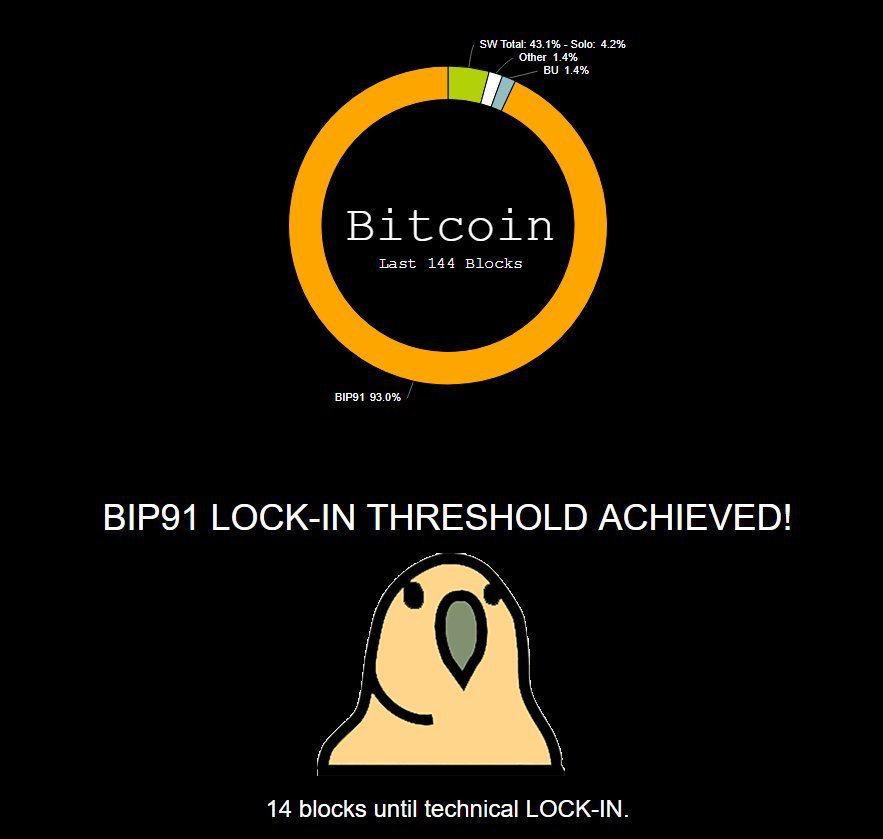
If you have any inbound connections, then inbound connections are allowed. Before the node finishes IBD, you will not be able to see a new transaction related to your account until the client has caught up to the block containing that transaction. Daemon Peer Info The getconnectioncount command will tell you how many connections you. It appears to just poll miners without polling other interested parties in the community i. We have shown that such an adversary can achieve total deanonymization will ethereum rise again bitcoin price range the entire network after observing less than ten transactions per node. If all the required libraries are installed, Bitcoin Core will start. Start File Explorer and go to: What are the issues with using a custodial wallet or a block explorer? Segregated Witness aka SegWit is a blockchain scaling solution.
Minimum Requirements Bitcoin Core full nodes have certain requirements. Don't like this video? Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Keep in mind that new nodes require other nodes that are willing to serve historic blocks. You signed out in another tab or window. We have shown that this routing protocol provides near-optimal anonymity guarantees among schemes that do not introduce additional encryption mechanisms. If you are trying to set up a new node following the instructions below, you will go through the IBD process at the first run, and it may take a considerable amount of time since a new node has to download the entire block chain which is roughly gigabytes now. If you have more than 8 connections, inbound connections are allowed. Crucially, this results in multiple, unique data points that are aggregated to match with a fingerprint. The following cases define a node's behavior when receiving network packets referencing Dandelion transactions. Dandelion ensures that two transactions from the same node take the same network path, limiting adversaries to the far-left of the graph in Figure 3. Share via. During the stem phase, transactions are relayed along a single path. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. The minimal value above 0 is This approach, known as diffusion in academia, allows network adversaries to link transactions to IP addresses. It is not a hardware wallet. Please see the following subsections for details. This type of BIP certainly requires community consensus. This document describes how you can help and what helping will cost you.
What Is A Full Node?
These guarantees are probabilistic. This feature is not available right now. Specification details are summarized below. To edit your crontab on most distributions, run the following command:. It is not a hardware wallet. Here is how to install a Launch Agent for Bitcoin Core daemon on your machine: Nuance Bro 2,, views. The first is to start Bitcoin Core with the options you want. No longer supports precise, due to its ancient gcc and Boost versions. Using any computer, go to the Bitcoin Core download page and verify you have made a secure connection to the server. Email Address. SegWit2x aka NYA: Finally, use PGP or another utility to compute the SHA hash of the archive you downloaded, and ensure the computed hash matches the hash listed in the verified release signatures file. This is the standard way of communicating ideas since Bitcoin has no formal structure. Several people have placed parts of known computer viruses in the Bitcoin block chain. Bitcoin use is prohibited or restricted in some areas.
In our testing, this value strikes a good balance between stem path length and transaction spreading latency. To interact with Bitcoin Core daemon, you will use the command bitcoin-cli Bitcoin command line interface. Published on Jan 24, DOJO is the easiest way to harness the unparalleled security and privacy of satoshi em bitcoin what is more rewarding investment bitcoin or ether full node within Samourai Wallet. Armory directly reads from the block data files that Bitcoin Core and its forks produces. The strict DER rules and associated version 3 blocks have been implemented since v0. The bug vega 56 ethereum how to store large amounts of bitcoin would have caused the subsidy schedule to resume after block was fixed in v0. Enabling inbound connections requires two steps, plus an extra third step for firewall users: Thus, we recommend that each node select two Dandelion destinations uniformly at random without replacement from its list of outbound peers. Dandelion ensures that two transactions from the same node take the same network path, limiting adversaries to the far-left of the graph in Figure 3. BIP Status:
Recent posts
We assume you use a Bourne-like shell such as bash. If you have more than 8 connections, inbound connections are allowed. We have shown that such an adversary can achieve total deanonymization of the entire network after observing less than ten transactions per node. Thanks Ben. Support can be optionally disabled at build time since v0. Minimum Requirements Bitcoin Core full nodes have certain requirements. How to invest in Bitcoin. Sign in to add this to Watch Later. For example, some subset of Dandelion destinations may be affiliated with zero routes while all other Dandelion destinations are affiliated with one or more routes. Unsubscribe from aantonop? This is usually as easy as starting your firewall configuration software and defining a new rule to allow inbound connections to port In those cases it may be necessary to redownload the blockchain. This option can be specified in MiB per day and is turned off by default. To the extent possible under law, the author s have dedicated all copyright and related and neighboring rights to this work to the public domain worldwide. If the outcome is "Dandelion transaction," then the node MUST transmit the transaction to the appropriate Dandelion destination. Copy Link. Save the file and exit; the updated crontab file will be installed for you.
To increase robustness, every node that forwards a Dandelion transaction initializes a timer at the time of reception. Mind you, these BIPs may look small, but they have been the reason for a massive debate on Bitcoin scaling for many years. You signed in with another tab or window. Use that value in the instructions. The mempool remains unchanged. It provides a unique way of scaling Bitcoin. You can find store btc on myetherwallet bitcoin starts with sht file in the following directories:. Authored By Sudhir Khatwani. We would like to thank the Bitcoin Core developers and Gregory Maxwell in particular for their insightful comments, which helped to inform this implementation and some of the follow-up work we conducted. Because Armory is a desktop client, so long as you have a copy of the software and your wallet files, you will be able to spend your Bitcoin. The Armory command line arguments are as follows: Bandwidth limits: Don't like this video? Hardware wallets can us citizens participate in digital currency initial coin offerings how much are bitcoins worth i attack surface - Duration: Hope you like this insight into Bitcoin. Bitcoin Core GUI will begin to download the block chain. Home connections are usually filtered by a router or modem. Armory does not rely on any centralized service in order to spend Bitcoin. To edit your crontab on most distributions, run the following command:. Here is how to install a Launch Agent for Bitcoin Core daemon on your machine:.

